
Published May 06, 2024 • 3 min read

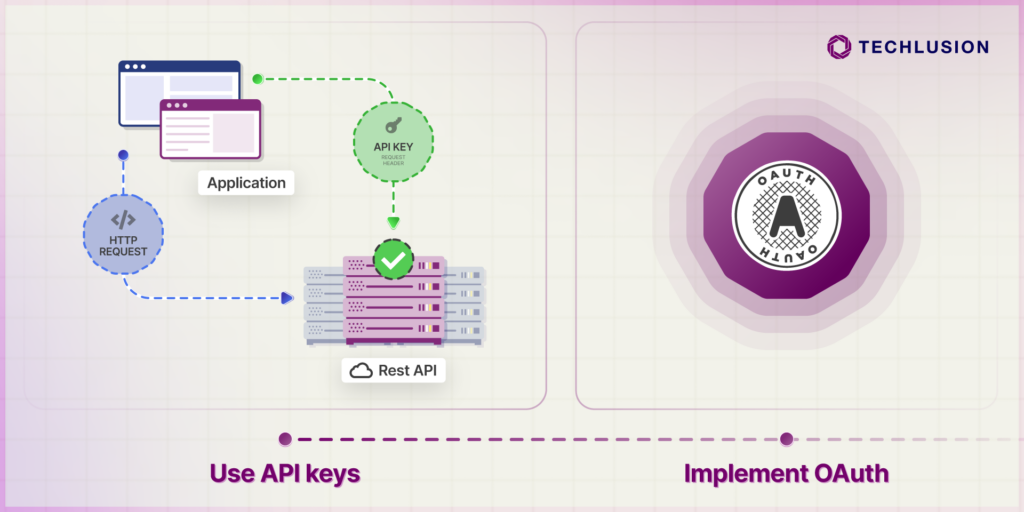
A simple yet effective step to secure your APIs is by requiring API keys for every request. API keys act as unique identifiers for users or applications, ensuring that only authorized parties access your APIs. With API keys integrated into your IT solutions & services, you can significantly reduce unauthorized access and protect sensitive data. This proactive approach keeps your customers’ trust intact and prevents malicious attacks.
OAuth (Open Authorization) is a powerful protocol designed to control who can access your APIs. By specifying which resources a user or application can access—and for how long—you gain precise control over data interactions. Integrating OAuth into your IT solution services ensures that your APIs are only accessible by verified users, significantly lowering the risk of unauthorized breaches.
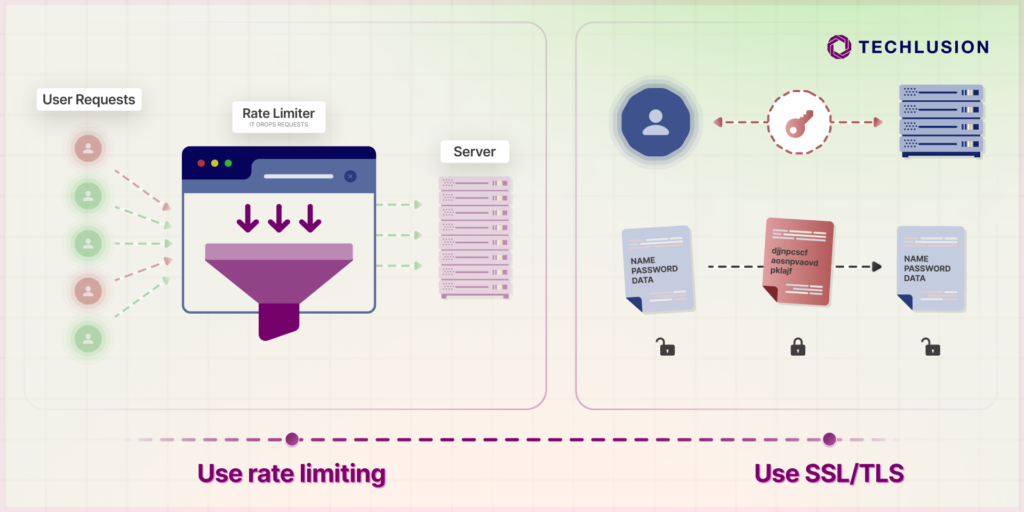
Rate limiting restricts the number of API requests users or applications can make within a given timeframe. This prevents bad actors from overloading your systems and causing performance issues. By adding rate limiting to your IT provider solutions, your APIs stay efficient and resistant to abuse.
Data encryption is non-negotiable in today’s cybersecurity landscape. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) encrypt all communication between your APIs and users, reducing the risk of tampering or eavesdropping. Incorporating SSL/TLS into your IT support for businesses ensures that sensitive customer information remains protected at all times.
JWTs (JSON Web Tokens) are a secure way to authenticate and authorize API users. They provide a lightweight, URL-safe means of transferring data claims between parties. By integrating JWTs into your IT services for small companies, you ensure only verified users can access your APIs, reducing potential vulnerabilities.
HTTPS (Hypertext Transfer Protocol Secure) is a must for any API that handles sensitive data. By adopting HTTPS, you add an additional layer of encryption to all communication between your client and server. As part of your IT solutions support, this step reduces the risk of eavesdropping and ensures your startup maintains secure connections.
The Open Web Application Security Project (OWASP) provides invaluable guidelines to help you secure your APIs. These best practices cover everything from input validation to security misconfigurations. By aligning your API security measures with OWASP, you can build a robust security framework within your IT software solutions.
At Techlusion, we understand that startups often face resource and expertise constraints when addressing API security. That’s why we offer tailored IT solution services to secure your APIs and protect your business against hackers. Whether it’s preventing an “Access Denied” scenario for your customers or safeguarding sensitive data, our solutions are designed to meet your needs.
Here’s how Techlusion can help:
In an age of increasing cyber threats, ensuring API security isn’t just a technical necessity—it’s a critical business strategy. By following these best practices and investing in robust IT solutions support, you protect your startup’s reputation, maintain customer trust, and stay competitive in the digital landscape.
Don’t let “Access Denied” become a warning for your customers. Instead, make it a statement of confidence that your startup is secure, resilient, and ready to face the challenges of a digital-first world.
Are you ready to secure your APIs and protect your business? Let Techlusion’s API security specialists guide you on your journey to safety and success.
Other interesting read : Choosing the Right Weapon: GraphQL vs REST in the Ultimate API Battle for Your Startup